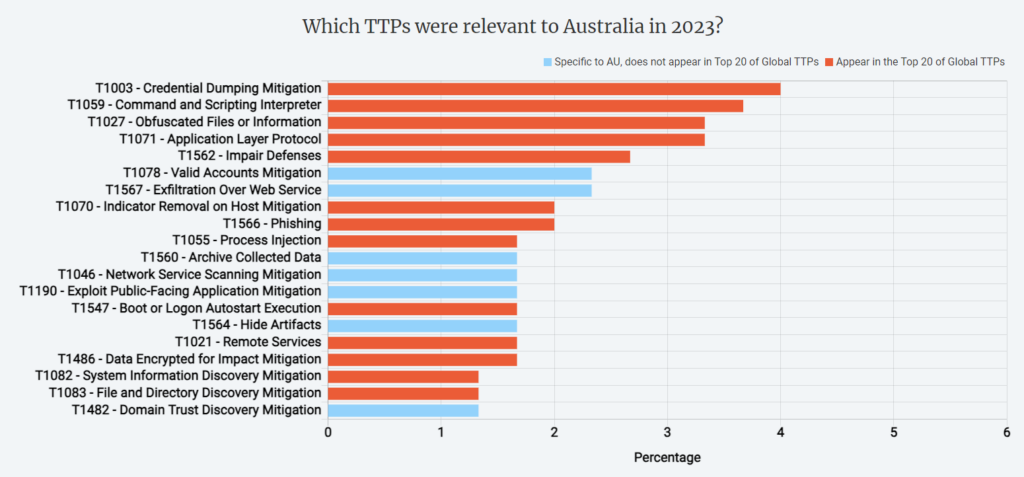
Top 20 TTPs in 2023: Australia compared to the World
Jan 22, 2024
This retrospective analysis of the tactics, techniques, and procedures (TTPs) employed by cybercriminals is conducted to assist cybersecurity professionals in planning how to fortify their defence strategies. The analysis sheds light on the top 20 TTPs specific to Australia, derived from RST Cloud’s thorough examination of cyber threats in 2023 based on RST Report Hub data, and compares them with the TTPs that were recognised as the top 20 globally in 2023.
Insights from the Analysis:
- Credential Dumping, Phishing and other user connected risks indicates a common cybersecurity risk shared with the global threat landscape.
- As well as injections, data obfuscation, information discovery and etc which is recognised as a significant TTP, emphasising the importance of safeguarding sensitive data.
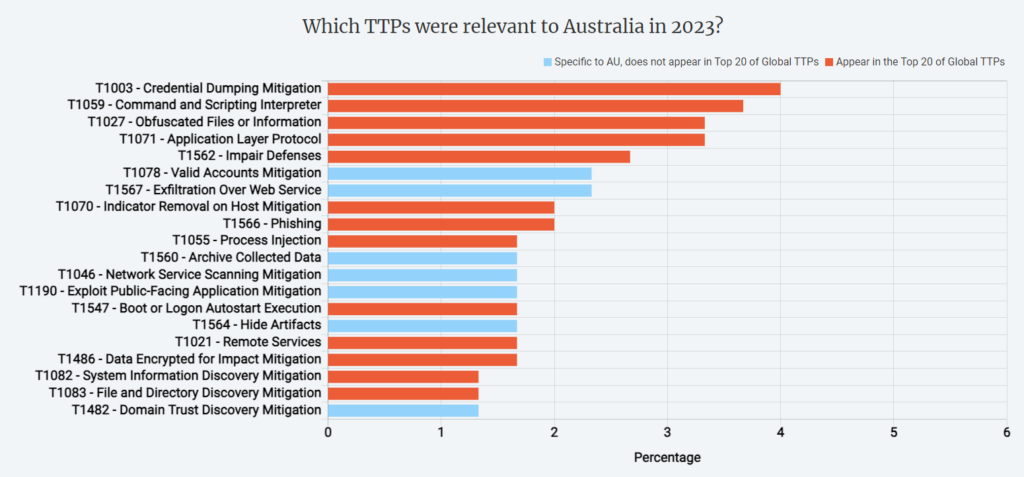
Unique Weaknesses and Divergence from Global TTPs:
Australia faces an increasing number of active attacks related to the exploitation of network services by intruders (scanning and exploits mitigation, absence of the user execution TTP in the top 20). Also, there are evident cyber hygiene issues, with valid account takeovers being identified as a common problem. Furthermore, threat actors are inclined to steal information and perform exfiltration through web services, all while concealing artifacts and collected data.
Noteworthy is the absence of certain global TTPs in the Australian Top 20 context, including masquerading and obfuscating, scheduled task mitigation, and sandbox evasion techniques. Attackers might be successfully exploiting simpler attack vectors, possibly due to gaps in security practices or lack of awareness. In such a case, it’s crucial for organisations to recognize and address these issues promptly.
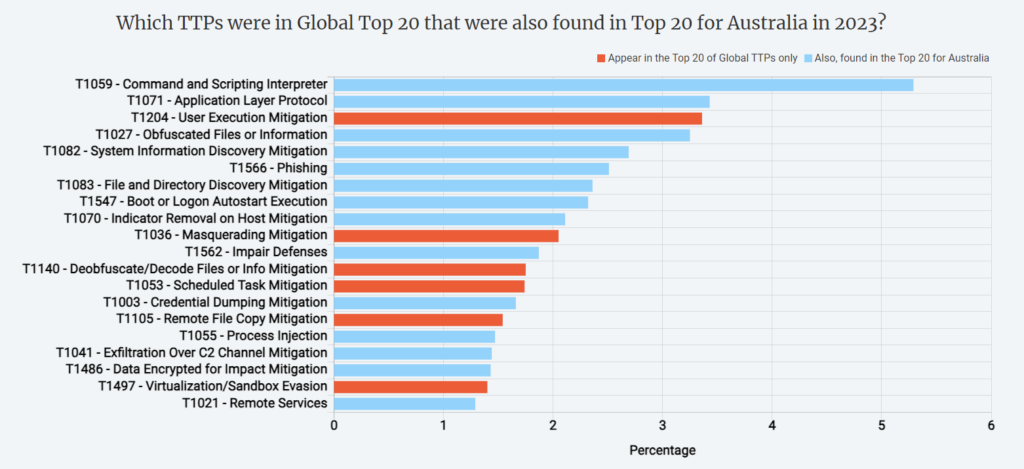
Understanding the specific TTPs relevant to Australia is crucial for cybersecurity experts and strategists in formulating effective priorities. By aligning defensive measures with the unique threat landscape, organisations can enhance their resilience against cyber threats.
Conclusion:
As cybersecurity threats continue to evolve, staying informed about the TTPs most relevant to a specific region is paramount. This analysis of the top 20 TTPs for Australia provides valuable insights for cybersecurity professionals, that can serve as a foundation for robust defence strategies and proactive threat mitigation.