
Threat Hunting Essential Steps and Key Components
Threat hunting is a proactive cybersecurity practice aimed at detecting, investigating, and mitigating advanced threats that may evade traditional security tools such as firewalls and antivirus software. Unlike reactive approaches like incident response, which wait for alerts from systems, threat hunting actively searches for potential threats by looking for patterns, anomalies, and behaviors in networks, systems, and endpoints.
Key Components of Threat Hunting
- Hypothesis-Driven: Hunters often start with a hypothesis, made from CTI research, such as a known tactic used by an adversary (TTPs), and look for signs of it in the environment.
- Indicators of Compromise (IoCs) and Indicators of Behaviour (IoB): Hunters use IoC/IoBs like unusual IP addresses, malicious domains, and unexpected changes in files or system behaviour as clues to potential attacks.
- Advanced Tools: Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and specialised threat intelligence platforms (TIP) are commonly used for detecting, correlating, and analysing suspicious activity.
Why is Threat Hunting Needed?
- Prevent Advanced Threats: Some sophisticated threats (e.g., Advanced Persistent Threats, or APTs) can bypass automated detection systems. Threat hunting helps uncover these stealthy attacks.
- Reduce Dwell Time: The time between when a threat enters the network and when it’s detected (known as “dwell time”) can be shortened through proactive hunting, reducing the potential damage.
- Strengthen Defences: Threat hunters identify weaknesses in current security protocols and recommend improvements to harden systems against future attacks.
- Enhance Incident Response: Threat hunters can uncover evidence and details that improve the efficiency and effectiveness of incident response efforts, leading to faster mitigation and recovery.
In summary, threat hunting is a vital component of modern cybersecurity, helping organisations stay ahead of sophisticated threats and improving overall resilience. It complements traditional defences by going beyond reactive security measures to seek out and address unknown threats before they cause significant damage.
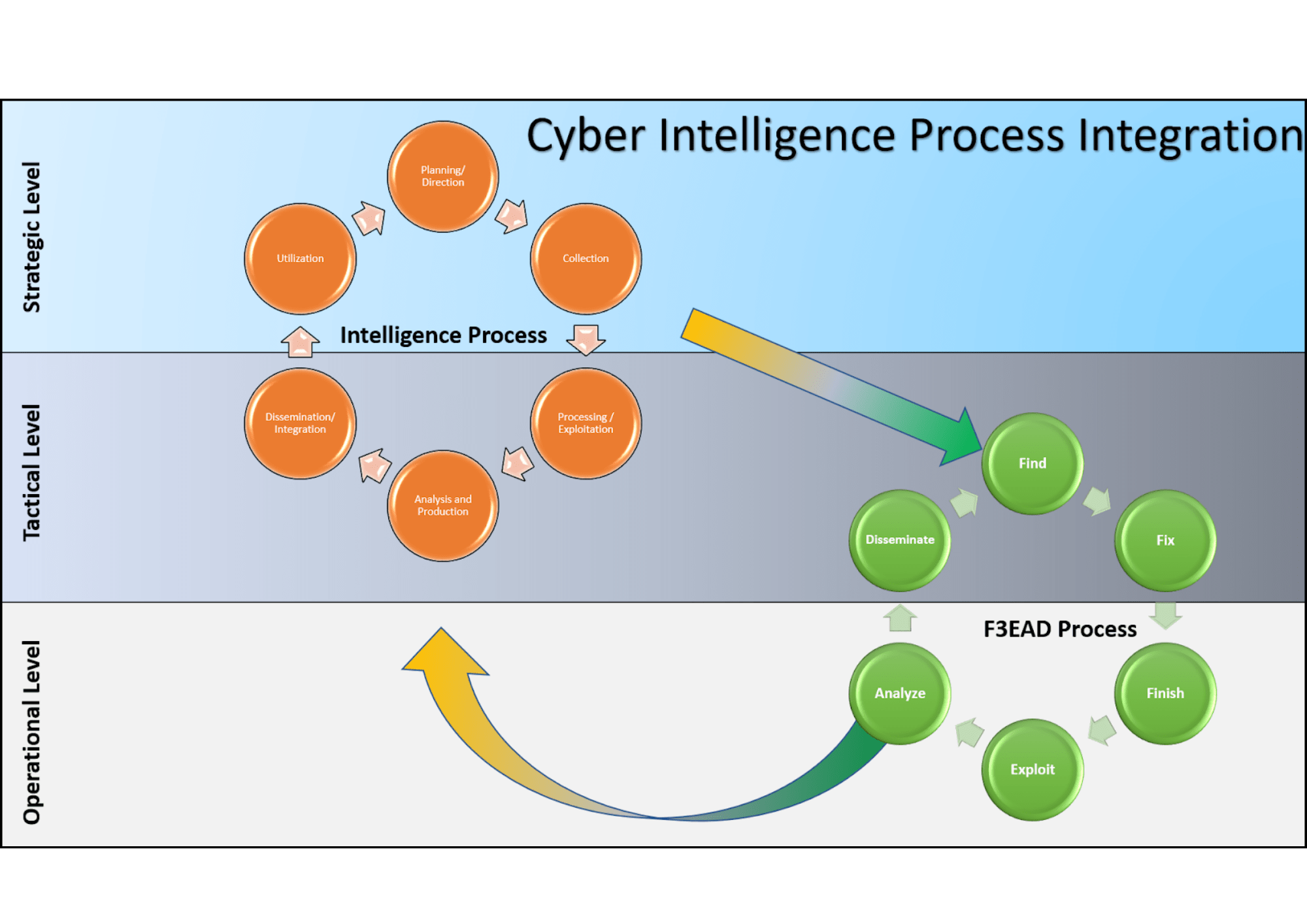
F3EAD or CTI Lifecycle?
When discussing Threat Hunting, it is often more effective to take a practical approach rather than strictly adhering to the CTI Lifecycle. In this context, we can refer to the F3EAD cycle, a methodology designed for rapid threat response, originally used in military and intelligence operations.
The F3EAD cycle stands for Find, Fix, Finish, Exploit, Analyse, Disseminate and is primarily used to address high-value targets. Its phases are as follows:
- Find: Identify potential threats through intelligence gathering.
- Fix: Pinpoint the exact location or details of the threat.
- Finish: Take action to neutralise or mitigate the threat. In cybersecurity, this could mean digital forensics or incident response.
- Exploit: Gather additional intelligence from neutralised threats, such as malware samples or compromised systems.
- Analyse: Examine collected intelligence to understand the adversary’s tactics, techniques, and procedures (TTPs).
- Disseminate: Share the insights with relevant stakeholders, including internal teams or external partners.
Although originally developed for military purposes, the F3EAD cycle is highly adaptable to cybersecurity. It is effective for threat hunting, incident response, and cyber threat intelligence (CTI) operations because it combines tactical actions with in-depth analysis and strategic sharing of findings. The cycle is particularly helpful in managing limited resources while responding swiftly to critical issues like data breaches or cyberattacks.
In essence, both CTI Lifecycle and the F3EAD cycle complement each other, providing a comprehensive approach to cybersecurity operations.
Advanced Threat Hunting with Priam AI Platform and RST Cloud
Priam AI Advanced Virtual Analyst (AVA) optimises your SOC operations within your existing ecosystem of products by leveraging data mining, machine learning, and AI techniques. The integration of RST Cloud services – RST Threat Feed, IoC Lookup, and Noise Control – brings additional tools to the Priam AI platform to increase platform efficiency and reduce alert fatigue. This joint solution can help reduce human errors, simplify incident triage complexity, and address the security talent shortage.
How is Threat Analysis process looks like with Priam AI AVA platform on practise:
Step 1. Find: Identifying targets or threats through intelligence gathering
- Define Objectives and Scope:
- Establish what you are hunting for (e.g., specific types of threats, advanced persistent threats, indicators of compromise) according to relevant threat landscape.
- Determine the scope of your hunt, including which systems, networks, or data will be included.
- Gather and Analyse Data:
- Collect relevant data from various sources such as logs, network traffic, endpoint data, and threat intelligence feeds.
- To facilitate effective analysis, ensure you have access to relevant sample data to inform your pivot – like RST Cloud CTI data.
RST Cloud aggregates and analyses a wide range of publicly available CTI data, including threat reports, community-driven intelligence, independent research, and more. Leveraging its own Honeypot network, C2 tracker, and partnerships with security companies and resources (including internet search engines and online sandboxes), RST Cloud collects and consolidates diverse threat intelligence knowledge. It then selects primary reports, extracts key facts and technical artifacts like IoCs, enriches each IoC with contextual information, and assigns a risk score. All IoCs are accessible through Priam AI platform.
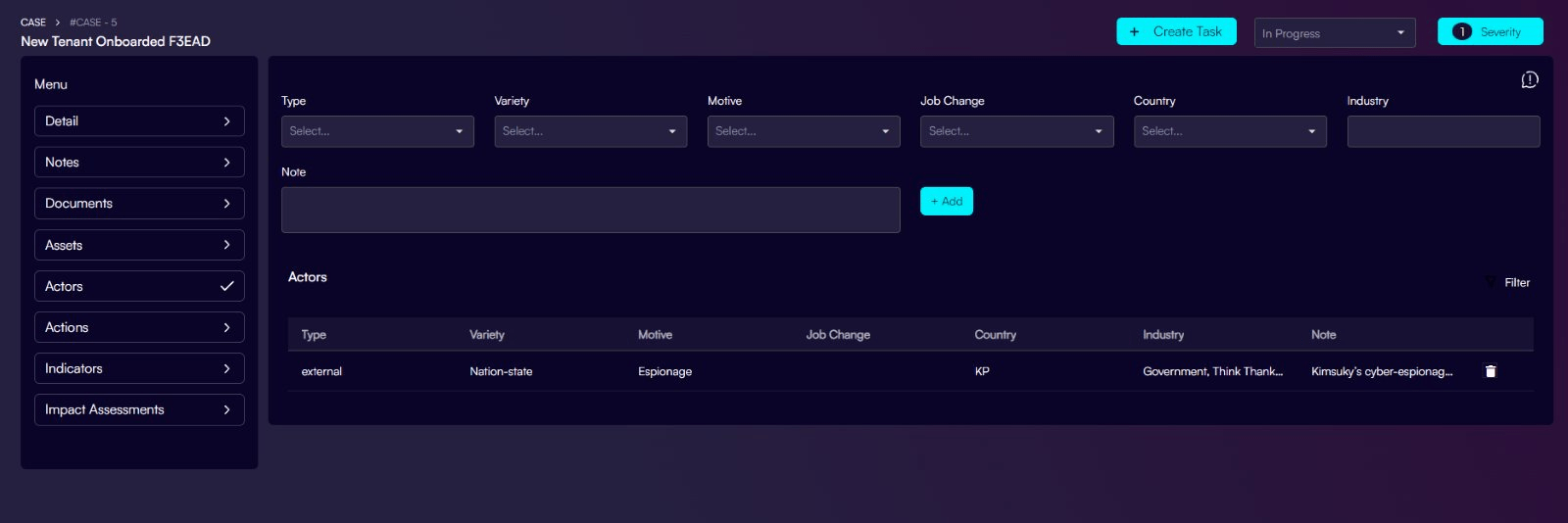
When you add and describe a new tenant (Company) in the Priam AI Platform, it automatically triggers the TI process to identify and analyse threat actors targeting the specified industry:
Step 2. Fix: Pinpointing the exact location or specifics of the threat
- Data Collection:
- Use threat intelligence platforms to gather data and formulate initial hypotheses. For example, analyse reports from the RST Report Hub to identify patterns and potential threats.
- Use threat intelligence and historical incident data to guide your hypotheses, working with the IoCs:
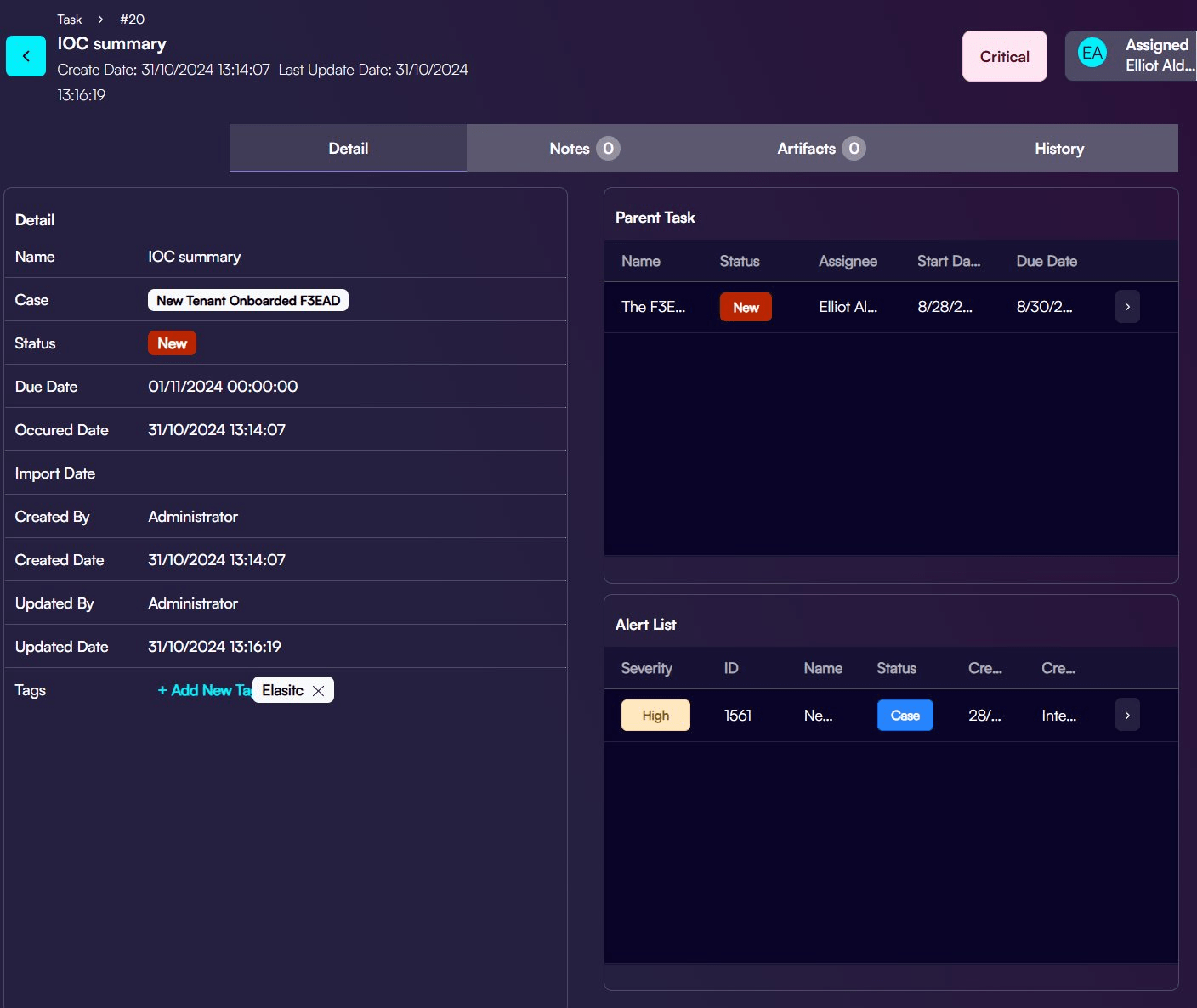
- Hypothesis Formulation:
- Develop hypotheses based on the collected data. These should be specific and actionable, such as “Could recent anomalies in network traffic be indicative of a new malware variant?”
Step 3. Finish: Taking action to neutralise or mitigate the threat, which could involve digital forensics or incident response in cybersecurity
- Initial Findings:
- If your initial search reveals potential threats, pivot to investigate further. This may involve tracing attack vectors, analysing malware samples, or examining compromised systems.
Step 4. Exploit: Collecting additional intelligence from the neutralised threat, such as malware samples or breached systems
- Behavioural Indicators and Anomaly Detection:
- Search for behavioural indicators that align with your hypothesis. Utilise advanced tools and AI-driven platforms like Priam AI for automated analysis and detection.
- Look for deviations from normal behaviour that might suggest malicious activity. This could involve analysing logs, network traffic, or system behaviours.
- Incident Sequencing:
- Construct a timeline of the incident to understand the sequence of events. This helps in uncovering the full scope of the attack and identifying any additional affected areas.
Generate a queries with AVA:
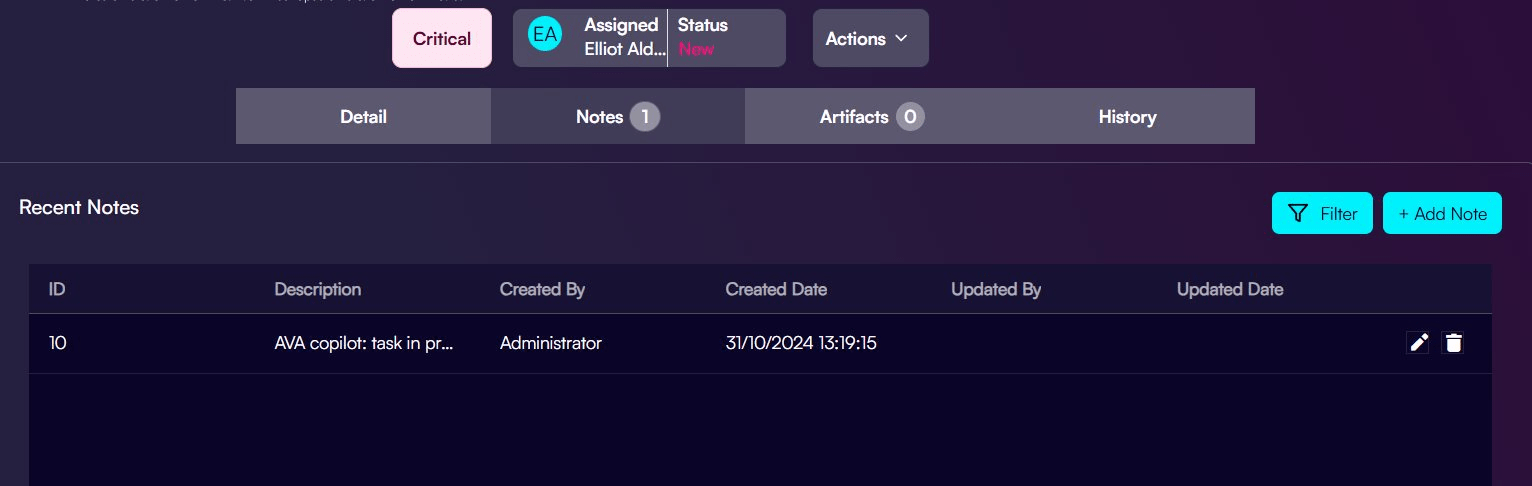
Step 5. Analyse: Thoroughly examining the collected intelligence to understand the tactics, techniques, and procedures (TTPs) used by the adversary
- Analysis and Documentation:
- Understand TTP used by adversaries.
- Compile a detailed report outlining your findings. This should include whether you identified a threat, the evidence supporting your findings, and any actions taken.
AVA Platform extracts the MITRE techniques used:
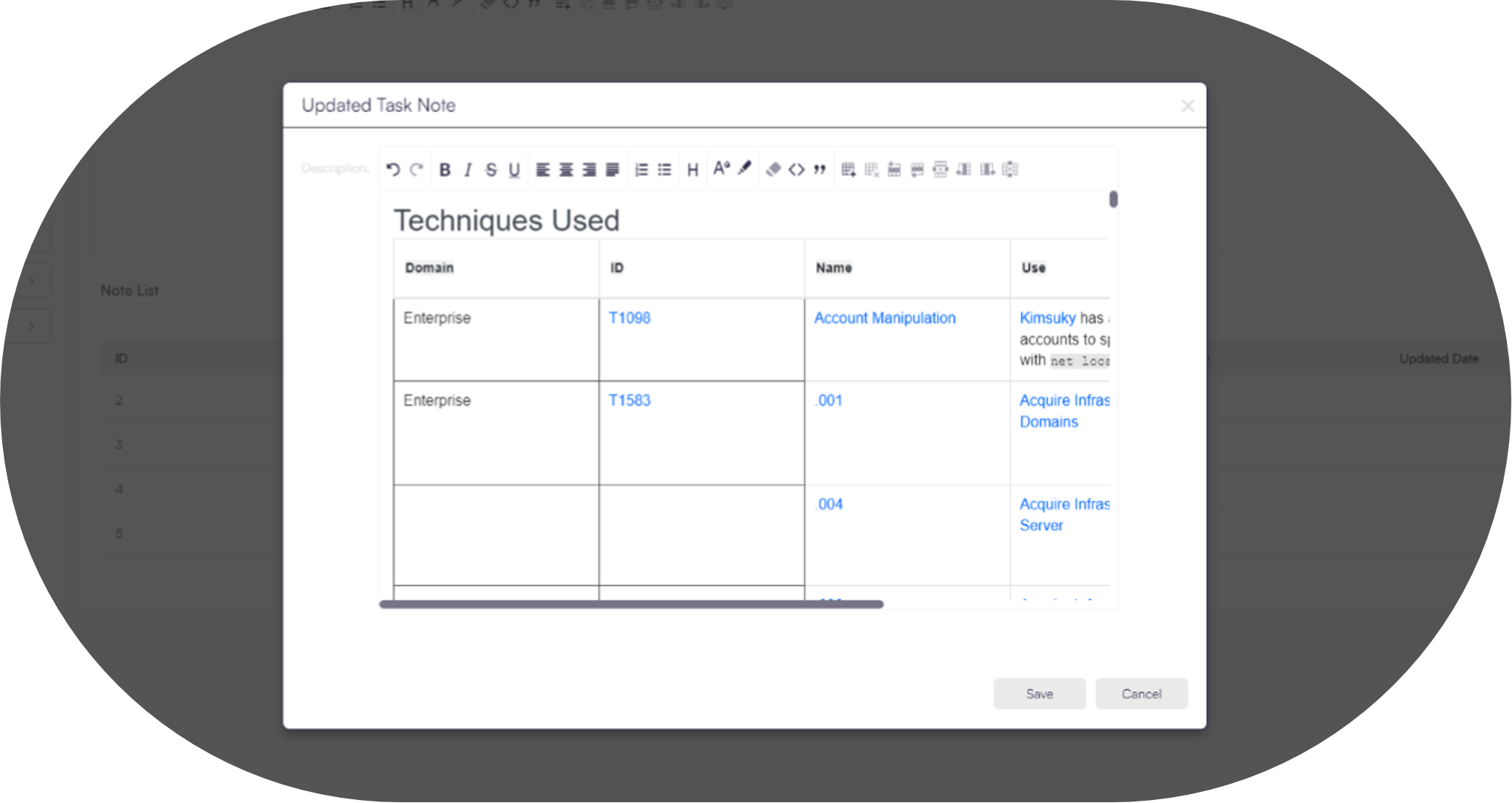
Step 6. Disseminate: Sharing insights with relevant stakeholders, including internal teams and external partners
- Sharing Insights and Feedback Loop:
- Share insights and recommendations to enhance future hunting efforts.
- Review the results with your team to refine your threat hunting processes.
Throughout the CTI process, the AI Assistant can support and enhance your efforts at each step:
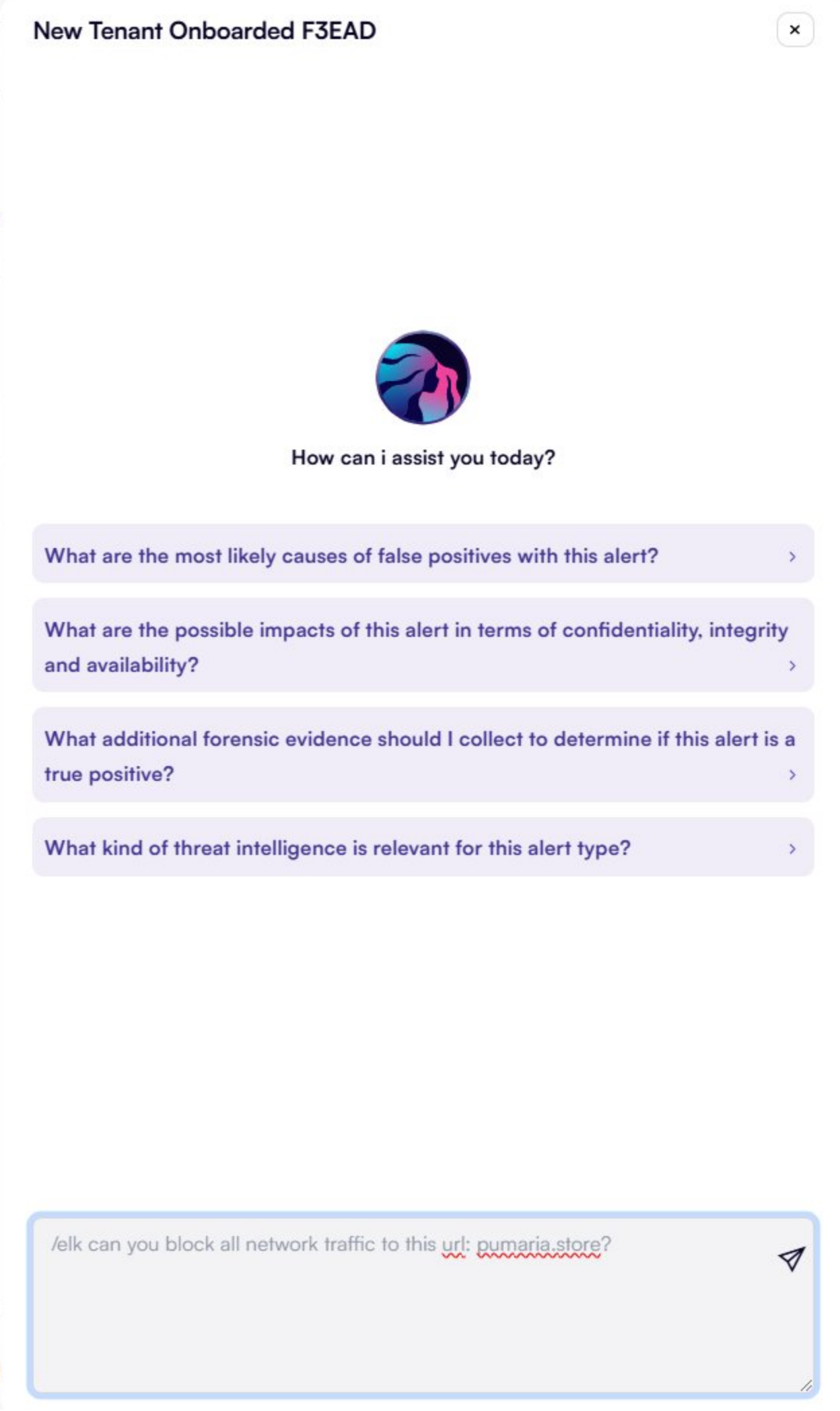
Evaluate what worked well and identify areas for improvement. Use these insights to refine your threat-hunting strategies and tools continuously. Regularly train your team on the latest detection techniques, and stay informed on emerging threats to integrate fresh intelligence into your practices.
For more information, contact us.