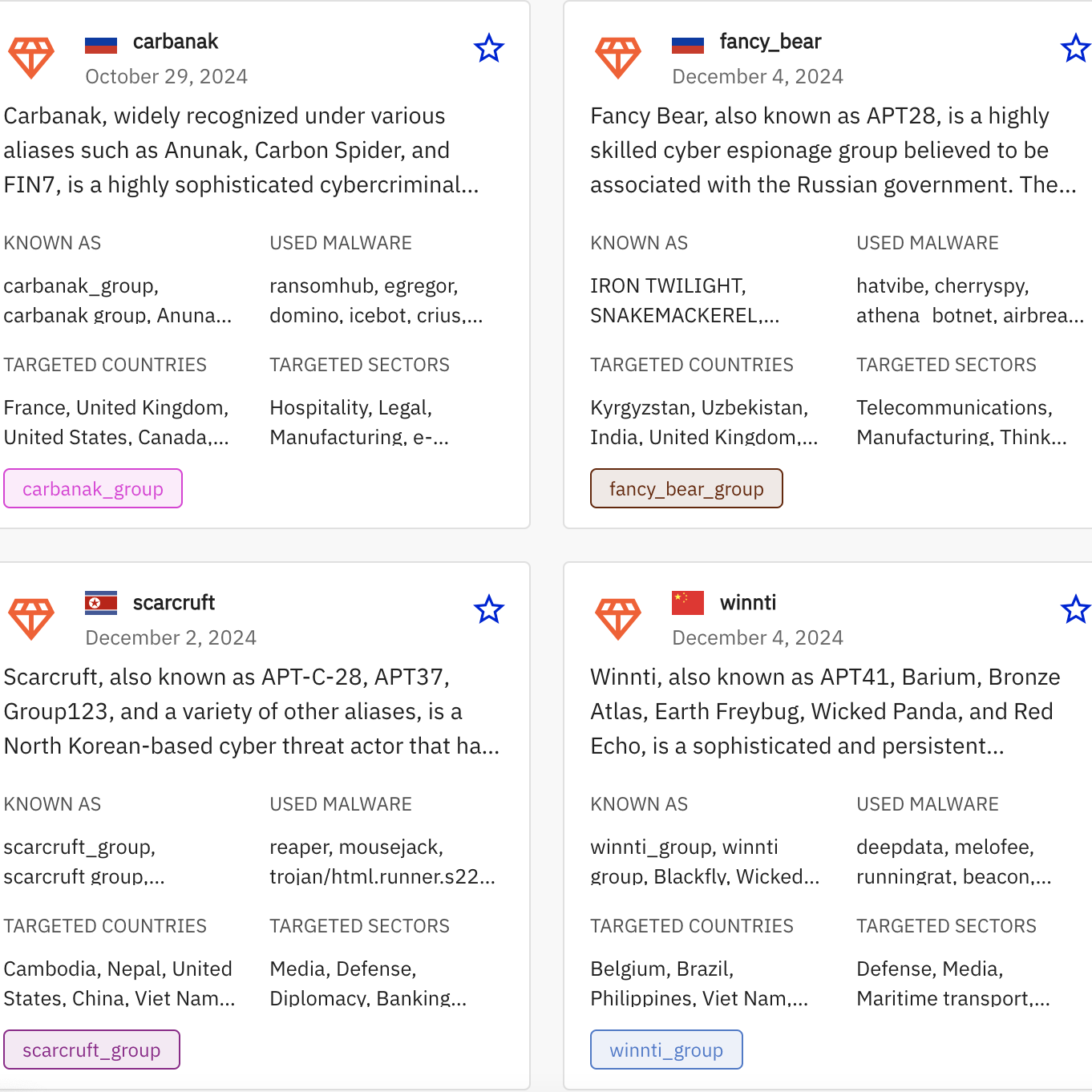
Features
Profiles in the RST Threat Library include detailed context and aliases of malware across various taxonomies used by different security vendors, such as:
Geolocation of adversaries, their objectives and motivations, common targets and behavioural tactics.
Descriptions of malware and common hacker tools, including information on how they work and what to look for.
Descriptions include external references to the original threat reports to support the statements.
5000+
Malware and Tools
850+
Intrusion Sets (threat actors)
STIX 2.1, JSON
Aliases, descriptions, and metadata
Actionable insights
Goals, motivations, comprehensive threat profiles, and operational details.
Use Cases
Problem:
Without a centralised threat knowledge base, analysts must often rely on fragmented sources, leading to inconsistent threat intelligence and potential blind spots in threat actors, malware, and tools.
Solution:
Continuously updated and contextualised RST Threat Library provides a single source of information and enhance threat visibility.
Problem:
Security researches often use different aliases and naming conventions for adversaries and malware, making it difficult for security teams to access a unified view of threat actors and their operations.
Solution:
RST Threat Library delivers a centralised, curated dataset of threat actors, malware, and tool names with their aliases and streamlines intelligence workflows.
Problem:
Without understanding how specific malware operates or the goals pursued by threat actors, analysts cannot quickly correlate alerts with known adversaries or malware.
Solution:
RST Threat Library provides insights into threat actor motivations, goals, and common targets, as well as known attack patterns, specific details on malware and hacker tools usage.
Problem:
The lack of insights into a threat actor’s objectives slows down appropriate containment and recovery actions during an incident.
Solution:
With the RST Threat Library, SOC teams gain access to detailed, structured, and continuously updated information on threat actors and their objectives enabling faster triage and more effective incident response.
Problem:
Without understanding the intent, capability, and opportunity of threat actors it is hard to prioritise threats that pose the most significant risk to an organisation.
Solution:
The well-structured RST Threat Library dataset enables CTI teams to prioritise threats and deliver detailed reports to stakeholders, including executive leadership, for informed decision-making on organisational risks.
Problem:
SOC analysts often lack an understanding of how specific malware or hacker tools operate, which slows them down as they search the Internet to identify what to do next.
Solution:
RST Threat Library provides descriptions of malware and tools to offer a quick understanding of what you are dealing with, helping to speed up triage, investigation, and incident response.
Request a Demo or Contact Us now.