Automate your Threat Intelligence Report Processing
Are you tired of spending countless hours processing hundreds of threat intelligence blogs, articles, and reports? Do you wish there was a way to easily extract critical information without manual analysis of endless pages?
RST Report Hub is here to change the game, with powerful automation that make processing of these reports a breeze.
Simple, Straightforward Pricing
You pay for an annual subscription and receive all the data you need.
No hidden fees, no matter how many CTI analysts use the service.
If you switch TI platforms, your data remains with you, with no additional costs for migration.
$1 500 per month
or $17 000 per year

Key Benefits
Save time and increase efficiency by automating processing of dozens of threat intelligence reports.
Access historical threat intelligence reports, even if they have been removed or become unavailable elsewhere.
Improve your threat detection and response capabilities with the critical data provided in the latest TI reports.
40000+
articles processed a year
2000+
CTI Reports/Year
STIX 2.1, PDF, JSON
Original reports and extracted metadata
TTPs/IOCs
Threat actors, campaigns, malware, CVE, TTP, Geo, industries, indicators, and more
What makes us different
Massive collection of threat intelligence reports organised as a library.
Our advanced parsing highlights key threat intel elements and standardises them in JSON and STIX formats.
A single, centralised location for accessing threat intelligence reports. No more time wasted searching for TI reports across many sources.
Rich metadata: TTPs, IOCs, attributed malware and APT groups, frameworks and software used by adversaries, vulnerabilities and so on.
A brief summary of the key points for each TI report, which significantly reduces the time to grasp the main idea.
Automatic transformation of texts into STIX 2.1 graphs
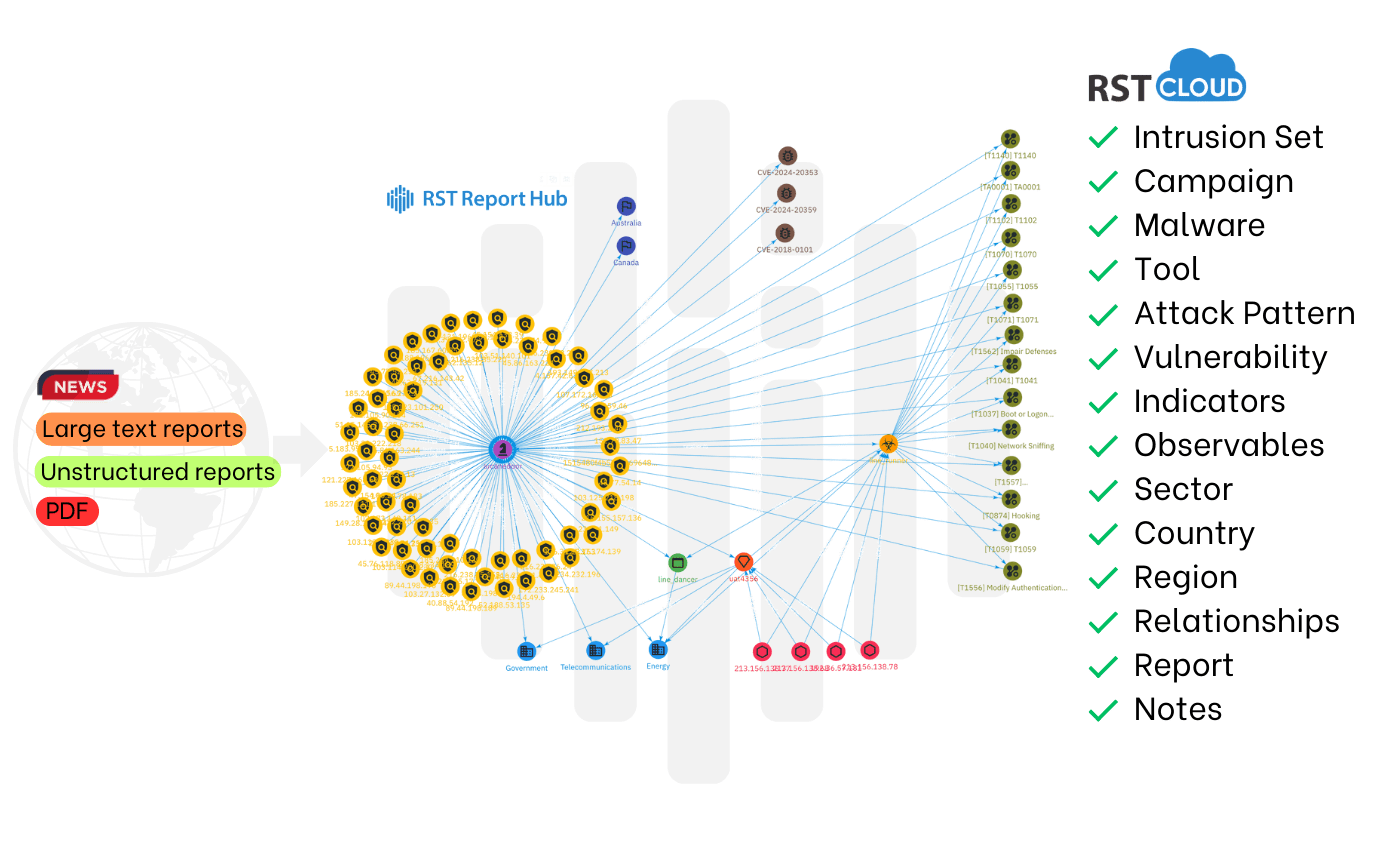
Usage Examples
Threat intelligence specialists use the centralised library of TI reports, making it easy to access the latest threat intelligence and provide insights to other teams.
SOC analysts can get valuable insights into the latest threats and vulnerabilities, enabling them to quickly identify and respond to potential security incidents.
Threat hunters can quickly access critical threat intelligence information to support their investigations and validate their hypotheses.
The TI report library can provide valuable insights to help incident response teams identify and contain the threat.
Risk management officers use the data to define current threat landscape and identify potential risks to their organisation.
RST Report Hub
{
"id": "20230501_tiprovider_123456_report_0x789abcde",
"date": "20230501",
"url": "https://tiprovide.example.com/en/12345",
"title": "Crypto-Mining Malware Discovered on Linux SSH Servers",
"img": "https://anon.example.com/wp-content/uploads/2023/04/04_hacked_04.png",
"cves": [
"CVE-2022-47966",
"CVE-2022-26134"
],
"threats": [
"kono_dio_da_campaign",
"xmrig_miner",
"shellbot",
"chinaz",
"kinsing_miner",
"log4shell_vuln"
],
"ttps": [
"ta0009",
"ta0002"
],
"industry": [
"healthcare",
"aerospace",
"education",
"energy",
"financial",
"government",
"telco"
],
"geo": [
"china",
"taiwanese",
"chinese",
"iranian",
"iran"
],
"softs": [
"microsoft defender for endpoint",
"microsoft defender",
"microsoft 365 defender",
"microsoft teams",
"azure active directory",
"confluence",
"active directory",
"active directory federation services",
"windows hello",
"windows firewall"
],
"program_languages": [
"perl",
"javascript"
],
"detects": {
"yara": true,
"sigma": false
},
"iocs": {
"ip": [
"12.34.56.78",
"98.76.54.32:80"
],
"domain": [
"mining.example.net:1444"
],
"url": [
"http://12.34.56.78/.bo/am"
],
"hash": [
{
"md5": "abcd1234efgh5678ijklmnopqrstuvwx"
}
]
},
"summary": "The short summary of the report - 2-3 mins to read",
"facts": "An ultra short abstract - 1 min to read",
"idea": "The main idea of the report",
"meta": {
"created": "auto",
"verified": false,
"translate": "auto"
}
}
{
"type":"bundle",
"id":"bundle--611416a5-85e8-4120-8003-141f162bff5c",
"objects":[
{
"type":"identity",
"spec_version":"2.1",
"id":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.540543Z",
"modified":"2024-04-13T01:26:31.540543Z",
"name":"unit42.paloaltonetworks.com",
"identity_class":"organization"
},
{
"type":"campaign",
"spec_version":"2.1",
"id":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.541869Z",
"modified":"2024-04-13T01:26:31.541869Z",
"name":"midnight_eclipse",
"aliases":[
"midnight_eclipse_campaign"
],
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"malware",
"spec_version":"2.1",
"id":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.54206Z",
"modified":"2024-04-13T01:26:31.54206Z",
"name":"upstyle",
"malware_types":[
"backdoor"
],
"is_family":true,
"aliases":[
"upstyle_backdoor"
],
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"attack-pattern",
"spec_version":"2.1",
"id":"attack-pattern--c70be43e-b7ac-5981-8cca-e86acf118fbf",
"created":"2024-04-13T01:26:31.542268Z",
"modified":"2024-04-13T01:26:31.542268Z",
"name":"T1059",
"x_mitre_id":"T1059"
},
{
"type":"attack-pattern",
"spec_version":"2.1",
"id":"attack-pattern--f7cd314c-fde2-5934-83c8-b929bbaa2142",
"created":"2024-04-13T01:26:31.542419Z",
"modified":"2024-04-13T01:26:31.542419Z",
"name":"T1064",
"x_mitre_id":"T1064"
},
{
"type":"attack-pattern",
"spec_version":"2.1",
"id":"attack-pattern--9cc055a3-eced-5991-9f14-6419d9c11d14",
"created":"2024-04-13T01:26:31.542549Z",
"modified":"2024-04-13T01:26:31.542549Z",
"name":"T1105",
"x_mitre_id":"T1105"
},
{
"type":"attack-pattern",
"spec_version":"2.1",
"id":"attack-pattern--44416aef-e655-5bc1-be63-b556e724a150",
"created":"2024-04-13T01:26:31.542701Z",
"modified":"2024-04-13T01:26:31.542701Z",
"name":"T1574",
"x_mitre_id":"T1574"
},
{
"type":"attack-pattern",
"spec_version":"2.1",
"id":"attack-pattern--61701e6b-a7e6-5149-82df-d65ed686cf9c",
"created":"2024-04-13T01:26:31.542833Z",
"modified":"2024-04-13T01:26:31.542833Z",
"name":"T1562",
"x_mitre_id":"T1562"
},
{
"type":"attack-pattern",
"spec_version":"2.1",
"id":"attack-pattern--f29f3c3a-a0dd-5afa-95ad-7abc1d3dcb4b",
"created":"2024-04-13T01:26:31.54296Z",
"modified":"2024-04-13T01:26:31.54296Z",
"name":"T1041",
"x_mitre_id":"T1041"
},
{
"type":"attack-pattern",
"spec_version":"2.1",
"id":"attack-pattern--71509424-7776-5097-bfb7-043821b480a1",
"created":"2024-04-13T01:26:31.543085Z",
"modified":"2024-04-13T01:26:31.543085Z",
"name":"T1070",
"x_mitre_id":"T1070"
},
{
"type":"vulnerability",
"spec_version":"2.1",
"id":"vulnerability--8f2989a7-26d8-5add-9d82-84fced078544",
"created":"2024-04-13T01:26:31.541724Z",
"modified":"2024-04-13T01:26:31.541724Z",
"name":"CVE-2024-3400",
"external_references":[
{
"source_name":"cve",
"external_id":"CVE-2024-3400"
}
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--432bde1e-edbb-5191-bd5e-6016becd7645",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.543228Z",
"modified":"2024-04-13T01:26:31.543228Z",
"name":"144.172.79.92",
"indicator_types":[
"malicious-activity"
],
"pattern":"[ipv4-addr:value='144.172.79.92']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.543228Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--e278ccc4-43b4-56f8-8696-dcdf66b20a50",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.544103Z",
"modified":"2024-04-13T01:26:31.544103Z",
"name":"66.235.168.222",
"indicator_types":[
"malicious-activity"
],
"pattern":"[ipv4-addr:value='66.235.168.222']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.544103Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--2df2d8b8-244a-5700-ab3a-cba3e22b3ea7",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.544774Z",
"modified":"2024-04-13T01:26:31.544774Z",
"name":"172.233.228.93",
"indicator_types":[
"malicious-activity"
],
"pattern":"[ipv4-addr:value='172.233.228.93']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.544774Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--4dc1981d-7896-5cc6-9cd1-4f51557b6f6b",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.545565Z",
"modified":"2024-04-13T01:26:31.545565Z",
"name":"nhdata.s3-us-west-2.amazonaws.com",
"indicator_types":[
"malicious-activity"
],
"pattern":"[domain-name:value='nhdata.s3-us-west-2.amazonaws.com']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.545565Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--7b0e1295-ea04-5bea-8d87-6a286ca463f3",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.54623Z",
"modified":"2024-04-13T01:26:31.54623Z",
"name":"http://172.233.228.93/policy",
"indicator_types":[
"malicious-activity"
],
"pattern":"[url:value='http://172.233.228.93/policy']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.54623Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--73604288-6ef0-5fc6-9bd5-0ccb01760755",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.563171Z",
"modified":"2024-04-13T01:26:31.563171Z",
"name":"http://144.172.79.92/update.py",
"indicator_types":[
"malicious-activity"
],
"pattern":"[url:value='http://144.172.79.92/update.py']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.563171Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--bcaedc33-93fa-507a-b073-e1bfab6a5a27",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.564205Z",
"modified":"2024-04-13T01:26:31.564205Z",
"name":"http://172.233.228.93/patch",
"indicator_types":[
"malicious-activity"
],
"pattern":"[url:value='http://172.233.228.93/patch']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.564205Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--26546636-f83a-5ec5-91dd-09c65905d770",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.564932Z",
"modified":"2024-04-13T01:26:31.564932Z",
"name":"3de2a4392b8715bad070b2ae12243f166ead37830f7c6d24e778985927f9caac",
"indicator_types":[
"malicious-activity"
],
"pattern":"[file:hashes.'SHA-256'='3de2a4392b8715bad070b2ae12243f166ead37830f7c6d24e778985927f9caac']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.564932Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"indicator",
"spec_version":"2.1",
"id":"indicator--5051894c-f70b-510e-8428-f596750cf0a4",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.565724Z",
"modified":"2024-04-13T01:26:31.565724Z",
"name":"5460b51da26c060727d128f3b3d6415d1a4c25af6a29fef4cc6b867ad3659078",
"indicator_types":[
"malicious-activity"
],
"pattern":"[file:hashes.'SHA-256'='5460b51da26c060727d128f3b3d6415d1a4c25af6a29fef4cc6b867ad3659078']",
"pattern_type":"stix",
"pattern_version":"2.1",
"valid_from":"2024-04-13T01:26:31.565724Z",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--d05d35d9-4cb1-5603-9fa2-07c29cd2592a",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.5829Z",
"modified":"2024-04-13T01:26:31.5829Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--ce69ebe2-f97c-5521-9ad0-ca590f884e20",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.583295Z",
"modified":"2024-04-13T01:26:31.583295Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"attack-pattern--c70be43e-b7ac-5981-8cca-e86acf118fbf",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--36c0e8a7-6775-5e6d-b414-3963a3476aee",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.583508Z",
"modified":"2024-04-13T01:26:31.583508Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"attack-pattern--f7cd314c-fde2-5934-83c8-b929bbaa2142",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--4beca15a-328f-5049-a7fa-1986fe5e34ba",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.583706Z",
"modified":"2024-04-13T01:26:31.583706Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"attack-pattern--9cc055a3-eced-5991-9f14-6419d9c11d14",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--f976658f-cb67-5d0a-a0ef-75c8dd759068",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.583902Z",
"modified":"2024-04-13T01:26:31.583902Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"attack-pattern--44416aef-e655-5bc1-be63-b556e724a150",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--3726569d-f4c4-5320-a2a1-d355e32987eb",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.58411Z",
"modified":"2024-04-13T01:26:31.58411Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"attack-pattern--61701e6b-a7e6-5149-82df-d65ed686cf9c",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--0b2d022f-d242-52bd-9030-8ae03f14f2f5",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.58442Z",
"modified":"2024-04-13T01:26:31.58442Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"attack-pattern--f29f3c3a-a0dd-5afa-95ad-7abc1d3dcb4b",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--8571b129-abbb-5ed6-ba40-18203cb37c9a",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.584868Z",
"modified":"2024-04-13T01:26:31.584868Z",
"relationship_type":"uses",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"attack-pattern--71509424-7776-5097-bfb7-043821b480a1",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--23754e72-65c9-54c4-98c0-e717c0bef7e1",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.585111Z",
"modified":"2024-04-13T01:26:31.585111Z",
"relationship_type":"targets",
"source_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"target_ref":"vulnerability--8f2989a7-26d8-5add-9d82-84fced078544",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--a099baee-a729-5d5b-b1bf-540e36ac5e47",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.585366Z",
"modified":"2024-04-13T01:26:31.585366Z",
"relationship_type":"uses",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"attack-pattern--c70be43e-b7ac-5981-8cca-e86acf118fbf",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--50da0823-1a3b-527b-b553-172ed721f66e",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.585573Z",
"modified":"2024-04-13T01:26:31.585573Z",
"relationship_type":"uses",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"attack-pattern--f7cd314c-fde2-5934-83c8-b929bbaa2142",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--dcf9ac1e-70a6-53e1-8545-ef1459deccbb",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.585817Z",
"modified":"2024-04-13T01:26:31.585817Z",
"relationship_type":"uses",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"attack-pattern--9cc055a3-eced-5991-9f14-6419d9c11d14",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--23458ec6-52bf-53c1-8736-dd6e93c7407b",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.586016Z",
"modified":"2024-04-13T01:26:31.586016Z",
"relationship_type":"uses",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"attack-pattern--44416aef-e655-5bc1-be63-b556e724a150",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--8f61266c-9492-549a-bcec-92737e5d9b46",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.586263Z",
"modified":"2024-04-13T01:26:31.586263Z",
"relationship_type":"uses",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"attack-pattern--61701e6b-a7e6-5149-82df-d65ed686cf9c",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--97b5c58d-e232-5024-9696-28e660b394a6",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.586485Z",
"modified":"2024-04-13T01:26:31.586485Z",
"relationship_type":"uses",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"attack-pattern--f29f3c3a-a0dd-5afa-95ad-7abc1d3dcb4b",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--7943e9fa-a5e2-579d-85cb-121337ffbced",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.586708Z",
"modified":"2024-04-13T01:26:31.586708Z",
"relationship_type":"uses",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"attack-pattern--71509424-7776-5097-bfb7-043821b480a1",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--4c7397ae-bbec-5f92-a075-201e46e6bd5f",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.586967Z",
"modified":"2024-04-13T01:26:31.586967Z",
"relationship_type":"related-to",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--4c7397ae-bbec-5f92-a075-201e46e6bd5f",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.587161Z",
"modified":"2024-04-13T01:26:31.587161Z",
"relationship_type":"related-to",
"source_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--7ac7da30-559d-5310-9a98-65193392a834",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.587473Z",
"modified":"2024-04-13T01:26:31.587473Z",
"relationship_type":"indicates",
"source_ref":"indicator--432bde1e-edbb-5191-bd5e-6016becd7645",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--ab373347-2af6-5414-982d-5ca54feff4f2",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.58771Z",
"modified":"2024-04-13T01:26:31.58771Z",
"relationship_type":"indicates",
"source_ref":"indicator--e278ccc4-43b4-56f8-8696-dcdf66b20a50",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--f68c9a9a-900d-5eb3-b669-77d0ea7aa7c1",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.587934Z",
"modified":"2024-04-13T01:26:31.587934Z",
"relationship_type":"indicates",
"source_ref":"indicator--2df2d8b8-244a-5700-ab3a-cba3e22b3ea7",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--7b53d14c-edfd-5c0c-a666-ec0416cace45",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.588176Z",
"modified":"2024-04-13T01:26:31.588176Z",
"relationship_type":"indicates",
"source_ref":"indicator--4dc1981d-7896-5cc6-9cd1-4f51557b6f6b",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--a8b0dbcd-3bdb-5d9e-9661-1d027b98b607",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.588427Z",
"modified":"2024-04-13T01:26:31.588427Z",
"relationship_type":"indicates",
"source_ref":"indicator--4dc1981d-7896-5cc6-9cd1-4f51557b6f6b",
"target_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--7272213c-eab4-503d-993c-d325ec2aaec5",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.588652Z",
"modified":"2024-04-13T01:26:31.588652Z",
"relationship_type":"indicates",
"source_ref":"indicator--7b0e1295-ea04-5bea-8d87-6a286ca463f3",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--f45f396f-feb9-5dce-a0c1-25e37c7d53a0",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.588951Z",
"modified":"2024-04-13T01:26:31.588951Z",
"relationship_type":"indicates",
"source_ref":"indicator--73604288-6ef0-5fc6-9bd5-0ccb01760755",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--cb4db7d5-f5b2-5e99-b880-c85b81f755d1",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.589177Z",
"modified":"2024-04-13T01:26:31.589177Z",
"relationship_type":"indicates",
"source_ref":"indicator--73604288-6ef0-5fc6-9bd5-0ccb01760755",
"target_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--17b445e3-ca34-54c2-beec-3e2bc956cf27",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.589567Z",
"modified":"2024-04-13T01:26:31.589567Z",
"relationship_type":"indicates",
"source_ref":"indicator--bcaedc33-93fa-507a-b073-e1bfab6a5a27",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--199c554e-3a60-5847-8d29-f2abac72af57",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.589823Z",
"modified":"2024-04-13T01:26:31.589823Z",
"relationship_type":"indicates",
"source_ref":"indicator--26546636-f83a-5ec5-91dd-09c65905d770",
"target_ref":"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--fe483c9d-8fc6-5152-99ae-8a8291d56f65",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.590036Z",
"modified":"2024-04-13T01:26:31.590036Z",
"relationship_type":"indicates",
"source_ref":"indicator--26546636-f83a-5ec5-91dd-09c65905d770",
"target_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"relationship",
"spec_version":"2.1",
"id":"relationship--15f27efe-4620-5327-9bf6-6f5d0dfcf403",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.590284Z",
"modified":"2024-04-13T01:26:31.590284Z",
"relationship_type":"indicates",
"source_ref":"indicator--5051894c-f70b-510e-8428-f596750cf0a4",
"target_ref":"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
},
{
"type":"note",
"spec_version":"2.1",
"id":"note--9684fe72-ad1f-5c56-8863-719227f845ea",
"created":"2024-04-13T01:26:31.541208Z",
"modified":"2024-04-13T01:26:31.541208Z",
"abstract":"The main idea of the text is that Palo Alto Networks and Unit 42 are actively monitoring and tracking a critical command injection vulnerability, CVE-2024-3400, in Palo Alto Networks PAN-OS software. The vulnerability allows attackers to execute arbitrary code with root privileges on the firewall. The text also discusses the exploitation of this vulnerability in Operation MidnightEclipse, involving the deployment of a backdoor known as UPSTYLE. Additionally, it highlights the actions taken by the threat actor, the functionality of the backdoor, and steps taken by Palo Alto Networks to address the issue and protect customers.",
"content":"Palo Alto Networks and Unit 42 are actively monitoring and tracking activity related to a critical command injection vulnerability identified as CVE-2024-3400 in Palo Alto Networks PAN-OS software. This vulnerability allows an unauthenticated attacker to execute arbitrary code with root privileges on the firewall and has a CVSS score of 10.0. The Palo Alto Networks team is collaborating with external researchers, partners, and customers to quickly and transparently share information about this issue. The exploitation of CVE-2024-3400 has been observed in what is named Operation MidnightEclipse. So far, it is believed that a single threat actor has been involved in exploiting this vulnerability, but there is a possibility that more threat actors may attempt exploitation in the future. After exploiting the firewall, the threat actor in Operation MidnightEclipse created a cronjob that would run every minute to access commands hosted on an external server. It is suspected that these commands were used to deploy a second Python-based backdoor known as UPSTYLE. The UPSTYLE backdoor was found hosted at different URLs and had a last modified date of April 7, 2024. The update.py file, which is part of the UPSTYLE backdoor, has multiple layers of functionality. It writes another Python script to a specific location, which in turn decodes and executes an embedded Python script with two functions named protect and check. The protect function is likely used for persistence, while the check function determines if the script is running before executing the functional backdoor. This backdoor can execute commands and mask its activities by altering log files. The threat actor running this backdoor also employed automation to swiftly overwrite output files to avoid detection. An analysis of the commands executed by the threat actor revealed activities such as copying configuration files to web application folders for exfiltration. Furthermore, the threat actor was observed receiving commands from a URL through the cronjob backdoor. Subsequently, the actor cleaned up by removing all files associated with the backdoors and deleting the cronjobs. Palo Alto Networks has shared these findings with the Cyber Threat Alliance (CTA) members to help them protect their customers and disrupt malicious cyber actors. Customers of Palo Alto Networks are encouraged to make use of product protections and updates to defend against this threat effectively.",
"object_refs":[
"report--3ba571d6-6129-540d-8443-af4e0f5e1db3"
]
},
{
"type":"note",
"spec_version":"2.1",
"id":"note--ba1cb500-6808-53b4-91b9-17b0d63355cb",
"created":"2024-04-13T01:26:31.541371Z",
"modified":"2024-04-13T01:26:31.541371Z",
"abstract":"Related software",
"content":"nginx, Ubuntu, crontab",
"object_refs":[
"report--3ba571d6-6129-540d-8443-af4e0f5e1db3"
]
},
{
"type":"note",
"spec_version":"2.1",
"id":"note--0a2fdda7-2bd5-5093-896d-d6a8c932f5ac",
"created":"2024-04-13T01:26:31.541516Z",
"modified":"2024-04-13T01:26:31.541516Z",
"abstract":"Related software languages",
"content":"python",
"object_refs":[
"report--3ba571d6-6129-540d-8443-af4e0f5e1db3"
]
},
{
"type":"report",
"spec_version":"2.1",
"id":"report--3ba571d6-6129-540d-8443-af4e0f5e1db3",
"created_by_ref":"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"created":"2024-04-13T01:26:31.540934Z",
"modified":"2024-04-13T01:26:31.540934Z",
"name":"Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"description":"Palo Alto Networks and Unit 42 are actively monitoring CVE-2024-3400, a critical command injection vulnerability in PAN-OS software with a CVSS score of 10.0. The vulnerability allows an unauthenticated attacker to execute arbitrary code with root privileges on the firewall. Exploitation of CVE-2024-3400 has been observed in Operation MidnightEclipse by a threat actor who deployed the UPSTYLE backdoor. The UPSTYLE backdoor has layers of functionality, including the execution of commands, altering log files, and employing automation to avoid detection. The threat actor was observed exfiltrating data by copying configuration files to web application folders and receiving commands from a URL through a cronjob backdoor. Palo Alto Networks has shared its findings with the Cyber Threat Alliance (CTA) to help protect customers against malicious cyber actors.",
"report_types":[
"threat-report"
],
"published":"2024-04-13T00:00:00Z",
"object_refs":[
"identity--b7f5420c-48b0-5539-b94e-5bf001b4f418",
"campaign--fb65cbf4-d777-5fcf-a66e-8297a5116e61",
"malware--871eff04-03c3-5e70-8528-72b5040784f3",
"attack-pattern--c70be43e-b7ac-5981-8cca-e86acf118fbf",
"attack-pattern--f7cd314c-fde2-5934-83c8-b929bbaa2142",
"attack-pattern--9cc055a3-eced-5991-9f14-6419d9c11d14",
"attack-pattern--44416aef-e655-5bc1-be63-b556e724a150",
"attack-pattern--61701e6b-a7e6-5149-82df-d65ed686cf9c",
"attack-pattern--f29f3c3a-a0dd-5afa-95ad-7abc1d3dcb4b",
"attack-pattern--71509424-7776-5097-bfb7-043821b480a1",
"vulnerability--8f2989a7-26d8-5add-9d82-84fced078544",
"indicator--432bde1e-edbb-5191-bd5e-6016becd7645",
"indicator--e278ccc4-43b4-56f8-8696-dcdf66b20a50",
"indicator--2df2d8b8-244a-5700-ab3a-cba3e22b3ea7",
"indicator--4dc1981d-7896-5cc6-9cd1-4f51557b6f6b",
"indicator--7b0e1295-ea04-5bea-8d87-6a286ca463f3",
"indicator--73604288-6ef0-5fc6-9bd5-0ccb01760755",
"indicator--bcaedc33-93fa-507a-b073-e1bfab6a5a27",
"indicator--26546636-f83a-5ec5-91dd-09c65905d770",
"indicator--5051894c-f70b-510e-8428-f596750cf0a4",
"relationship--d05d35d9-4cb1-5603-9fa2-07c29cd2592a",
"relationship--ce69ebe2-f97c-5521-9ad0-ca590f884e20",
"relationship--36c0e8a7-6775-5e6d-b414-3963a3476aee",
"relationship--4beca15a-328f-5049-a7fa-1986fe5e34ba",
"relationship--f976658f-cb67-5d0a-a0ef-75c8dd759068",
"relationship--3726569d-f4c4-5320-a2a1-d355e32987eb",
"relationship--0b2d022f-d242-52bd-9030-8ae03f14f2f5",
"relationship--8571b129-abbb-5ed6-ba40-18203cb37c9a",
"relationship--23754e72-65c9-54c4-98c0-e717c0bef7e1",
"relationship--a099baee-a729-5d5b-b1bf-540e36ac5e47",
"relationship--50da0823-1a3b-527b-b553-172ed721f66e",
"relationship--dcf9ac1e-70a6-53e1-8545-ef1459deccbb",
"relationship--23458ec6-52bf-53c1-8736-dd6e93c7407b",
"relationship--8f61266c-9492-549a-bcec-92737e5d9b46",
"relationship--97b5c58d-e232-5024-9696-28e660b394a6",
"relationship--7943e9fa-a5e2-579d-85cb-121337ffbced",
"relationship--4c7397ae-bbec-5f92-a075-201e46e6bd5f",
"relationship--4c7397ae-bbec-5f92-a075-201e46e6bd5f",
"relationship--7ac7da30-559d-5310-9a98-65193392a834",
"relationship--ab373347-2af6-5414-982d-5ca54feff4f2",
"relationship--f68c9a9a-900d-5eb3-b669-77d0ea7aa7c1",
"relationship--7b53d14c-edfd-5c0c-a666-ec0416cace45",
"relationship--a8b0dbcd-3bdb-5d9e-9661-1d027b98b607",
"relationship--7272213c-eab4-503d-993c-d325ec2aaec5",
"relationship--f45f396f-feb9-5dce-a0c1-25e37c7d53a0",
"relationship--cb4db7d5-f5b2-5e99-b880-c85b81f755d1",
"relationship--17b445e3-ca34-54c2-beec-3e2bc956cf27",
"relationship--199c554e-3a60-5847-8d29-f2abac72af57",
"relationship--fe483c9d-8fc6-5152-99ae-8a8291d56f65",
"relationship--15f27efe-4620-5327-9bf6-6f5d0dfcf403"
],
"labels":[
"yara_not_found",
"sigma_not_found",
"midnight_eclipse",
"iocs_found"
],
"external_references":[
{
"source_name":"RST Report Hub: [unit42.paloaltonetworks.com] Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400",
"url":"https://unit42.paloaltonetworks.com/cve-2024-3400"
}
],
"object_marking_refs":[
"marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"
]
}
]
}