Reducing Alert Fatigue: How RST Noise Control and OpenCTI Improve Threat Intelligence
Cybersecurity analysts are often overwhelmed with large volumes of data, which can make it challenging to distinguish between genuine threats and benign events. To address this issue, we are excited to announce the integration of our RST Noise Control service with OpenCTI (by Filigran), an cutting-edge threat intelligence platform.
Introducing RST Noise Control
RST Noise Control is a powerful service designed to help cybersecurity professionals reduce the false positive rate of their threat intelligence data. Our service allows users to check whether an potential indicator of compromise (IOC) or a batch of such values are “known-good” and should be considered noise. As a result of this check, users can receive:
- A reason why a value is considered known-good.
- A verdict such as “drop,” “change score,” or “not found.”
Our service engine operates with more than 130 rulesets and over 40 GB of individual exceptions, continuously developing and expanding.
RST Noise Control works with four main types of IoCs: IP, Domain, URL, and Hashes, significantly reducing alert fatigue and enhancing the efficiency of threat analysis.
Why Integrate RST Noise Control with OpenCTI?
OpenCTI is a robust platform that helps organisations manage and share their threat intelligence data. When working with multiple threat intelligence sources, it is a common problem to have certain level of false positives, which can make the triage process more time consuming.
By integrating RST Noise Control with OpenCTI, we bring together the strengths of both platforms, offering a more streamlined and efficient threat intelligence workflow.
Here are some of the key benefits of this integration:
- Reduced Noise: Automatically filter out benign indicators from your threat intelligence data, reducing the number of false positives and allowing analysts to concentrate on genuine threats.
- Improved Efficiency: Save time and resources by eliminating the need to manually sift through large volumes of data to identify noise.
- Enhanced Accuracy: Increase the accuracy of your threat intelligence by ensuring that only relevant and actionable indicators are considered.
- Streamlined Workflows: Seamlessly integrate RST Noise Control’s capabilities into your existing OpenCTI workflows, enhancing your overall threat intelligence process.
- Reduces Alert Fatigue: By filtering noise, RST Noise Control helps to reduce alert fatigue for SOC Analysts, ensuring that your team can focus on the most critical alerts.
How the Integration Works
The integration between RST Noise Control and OpenCTI is designed to be straightforward and user-friendly. It can be invoked automatically or manually. Here’s how it works:
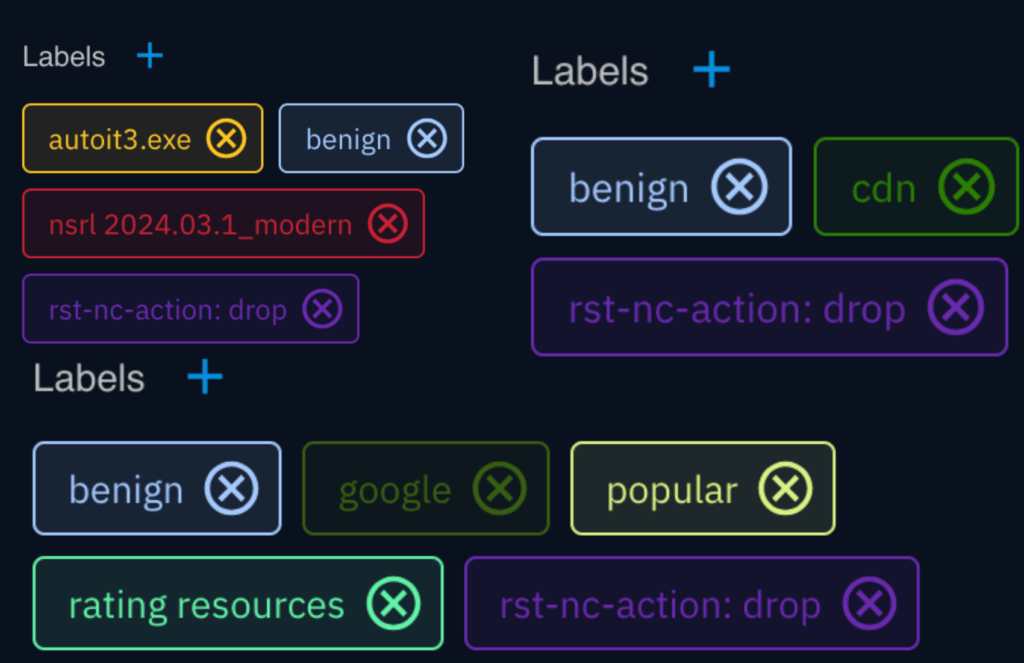
- Noise Filtering: RST Noise Control processes the ingested data to identify and filter out “known-good” indicators, marking them as noise.
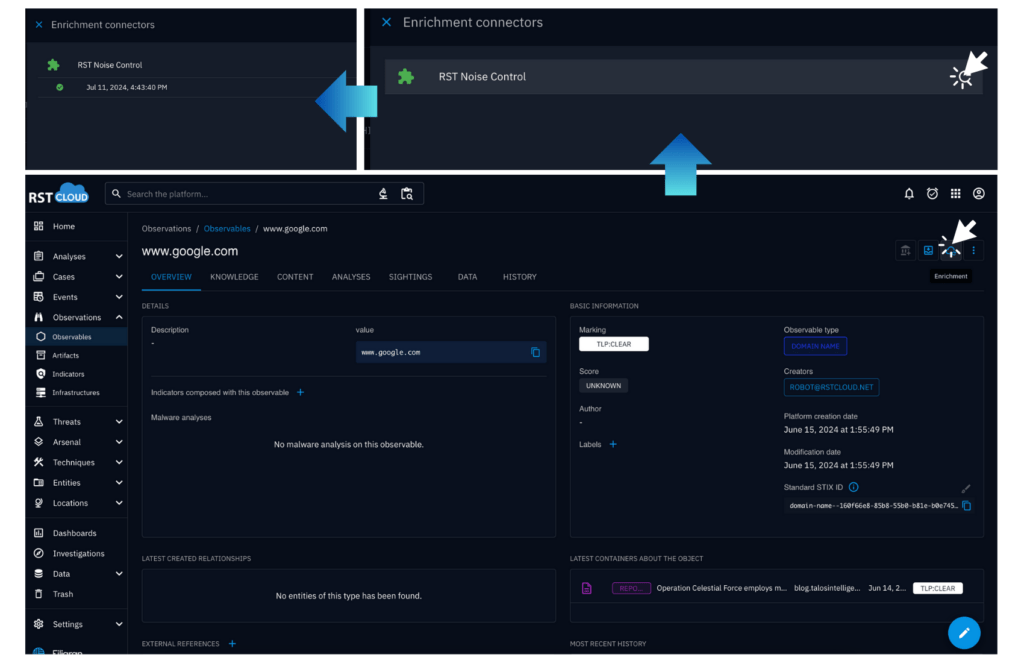
- Data Enrichment: The filtered data is enriched with additional context from RST Cloud’s extensive threat intelligence database, explaining why they are considered benign or warrant a lower risk score.
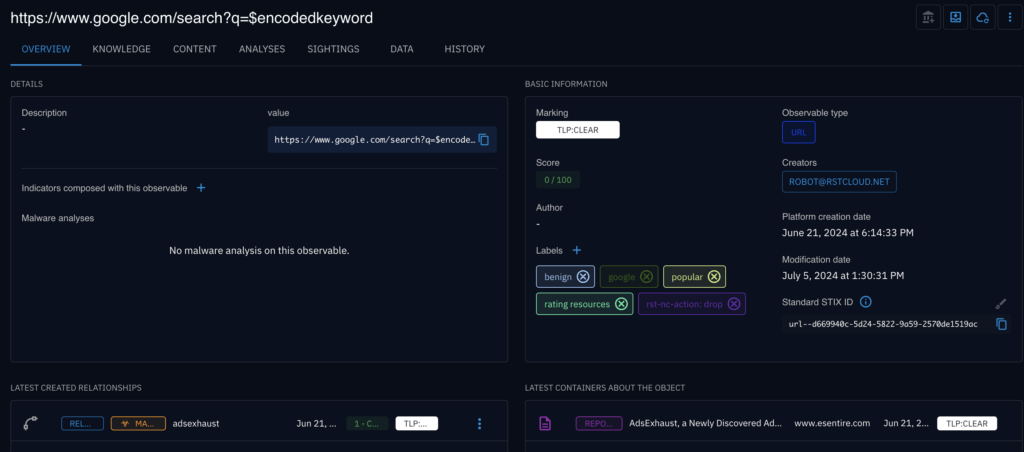
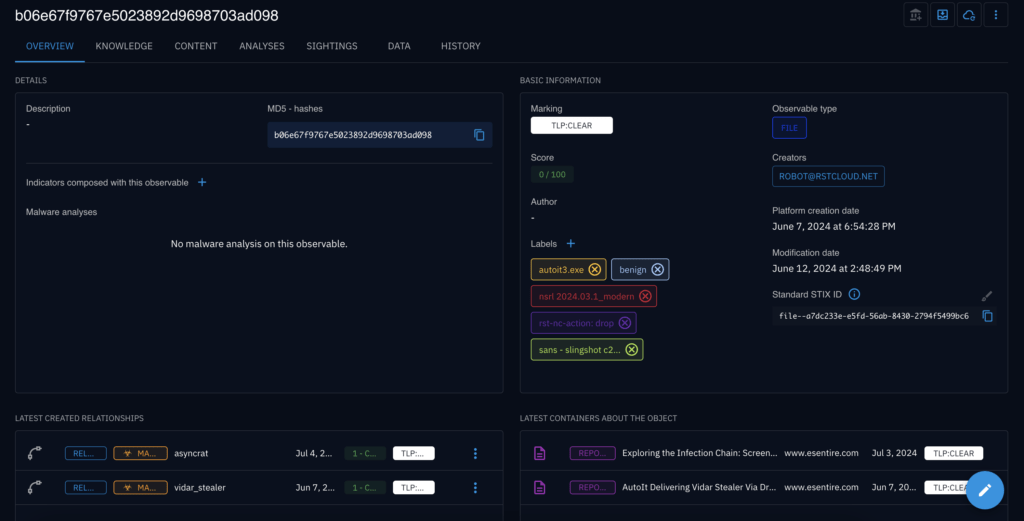
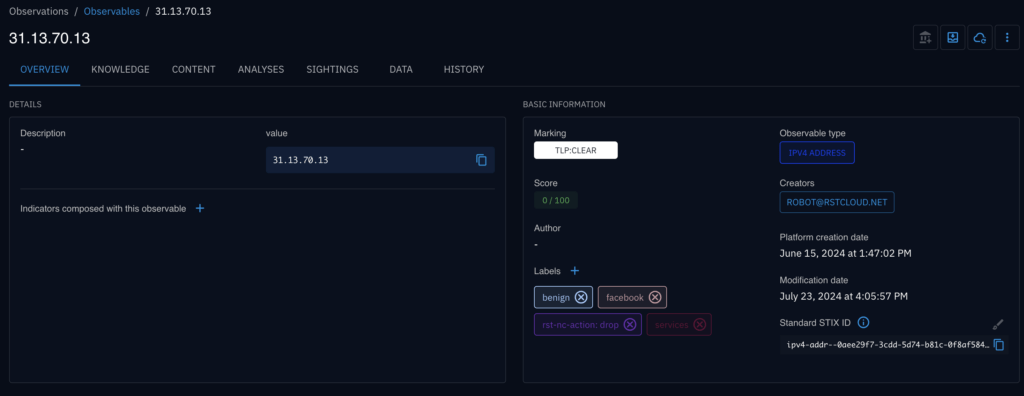
- Visualisation and Analysis: Analysts can visualise and analyse the refined threat data within OpenCTI, focusing on the most relevant and actionable information.
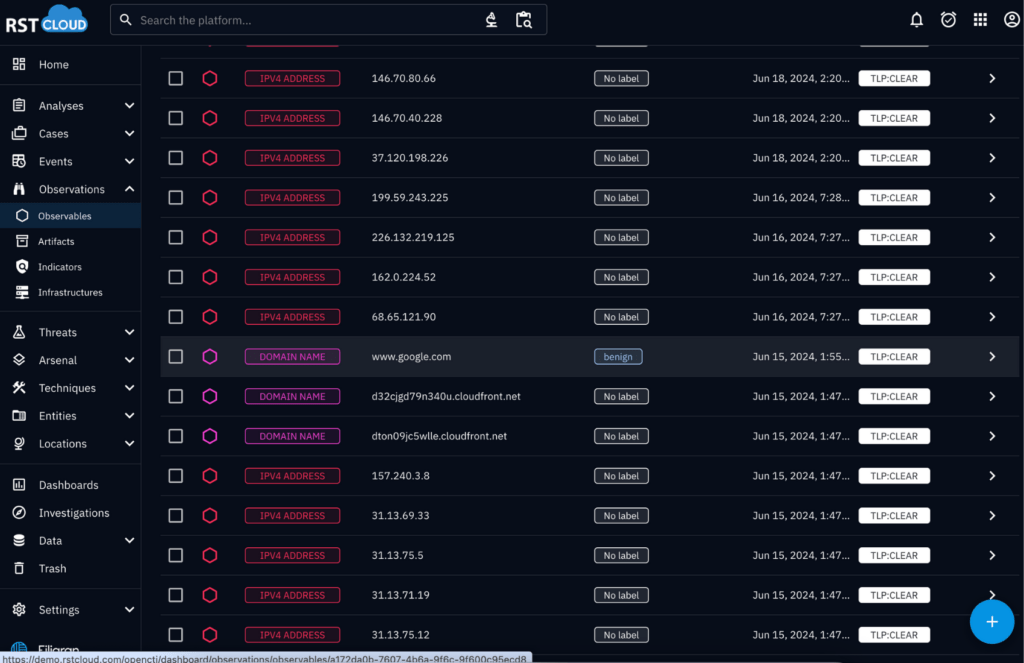
The integration supports automation of threat intelligence workflows, helping to streamline the process of threat detection and response.
Conclusions
The integration of RST Noise Control with OpenCTI offers a powerful solution for reduce False Positive rate in your threat intelligence data. By reducing noise and improving the accuracy of threat analysis, this integration empowers cybersecurity professionals to focus on what truly matters—protecting their organisations from genuine threats. We invite you to explore this integration and experience the benefits of a more efficient and effective threat intelligence workflow.
For more information and detailed setup instructions, contact us.