Guide to CTI: Roles, Evolution, and the Lifecycle
Nov 3, 2023
In the realm of cybersecurity, establishing a Cyber Threat Intelligence (CTI) function is not just a one-time task but a structured process. The initial step in this process involves setting the overarching objectives of the CTI function, defining the CTI roles, and determining the advantages it will bring to the organisation. Typically, these objectives encompass a blend of both technical and non-technical goals.
In crafting a CTI strategy for a department, it is essential to outline key objectives that encompass the following areas:
- Key Outputs: Clearly articulate the outputs that the CTI function will be responsible for delivering. These outputs may range from actionable threat intelligence reports to vulnerability assessments.
- Data Collection: Specify the types of information the CTI function will gather. This data could encompass indicators of compromise, historical attack patterns, or emerging threat actors.
- Threat Landscape: Understand and assess the threat landscape relevant to your organisation. Recognise the specific threats and risks that your company faces, which may differ based on industry, location, or the nature of your business.
- Outsourcing Considerations: Evaluate which components of the CTI function can potentially be outsourced. While some elements may require in-house expertise, others could be more efficiently managed by external partners or specialised services.
By addressing these key objectives and roles, an organisation can establish a robust CTI strategy that not only enhances its cybersecurity posture but also ensures alignment with its broader departmental goals.
The CTI team can be structured with the following three roles (which may not necessarily require three separate individuals) or integrated into other roles within the organisation:
- CTI Lead or Strategic Analyst: This role serves as the leader and manager of the CTI function, responsible for crafting and executing the strategy. Additionally, the CTI lead provides intelligence to senior management, the board, and system owners as needed.
| Audience Type*: | Strategic |
| Stakeholders: | Chief Information Security Officer Security and Risk Management |
| Tasks: | Allocate resources Identify key risks Communicate with executives |
| Problems: | No clear investment priorities Executives are not technical |
| Value-add from CTI: | Demystify threats Prioritise based on business risk |
- CTI Analyst (Operational goals): This analyst is tasked with the collection, analysis, and processing of information from non-structured sources, such as industry papers, TI Reports and channels etc. A lot of this work can be automated (see RST Report Hub). They also take on the responsibility of profiling the activities of threat actors identified in the threat assessment:
| Audience Type*: | Operational |
| Stakeholders: | SOC Manager SOC Analysts Incident Response Team Vulnerability and Patch Management Team Forensic Team Red and Purple Team |
| Tasks: | Determine attack vectors Prioritise patching and vulnerability remediation Build hypothesis on key risks for the organisation Share knowledge on the current threat landscape Assist other teams in making decision based on the knowledge about threat actors and their techniques |
| Problems: | Tons of news, reports, articles to read: processing of data is tedious Difficult to identify potential damage Difficult to prioritise patches |
| Value-add from CTI: | Add context to help in decision making for other teams Prioritise patches Focus in on potential targets Raise awareness |
- CTI Analyst (Technical Intelligence): Responsible for collecting, processing, and analysing technical intelligence, this analyst acts as the dedicated point of contact for the Security Operations Centre (SOC). While supporting the profiling of threat actors, their primary focus is on maintaining and delivering technical intelligence indicators, TTPs to the SOC and other defence teams:
| Audience Type*: | Tactical |
| Roles: | Security Operations Centre Network Operations Centre DFIR |
| Tasks: | Hunt for new adversary infrastructure Analyse malware Produce technical feeds Disseminate technical indicators to security tools |
| Problems: | False positives Alert overload |
| Value-add from CTI: | Validate and prioritise indicators Prioritise alerts |
As the process matures, these roles can evolve and be further refined. This may include the introduction of specialised teams such as Threat Research and Incident Response/Threat Hunting teams, legal and compliance officers, communications managers, and more, based on the organisation’s expanding requirements and resources.
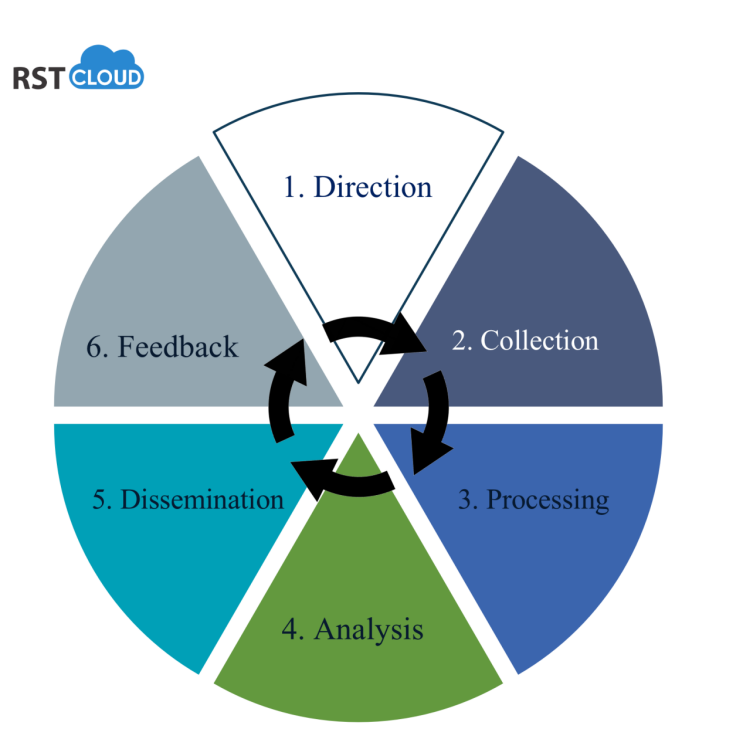
The workflow of CTI is well-defined within the threat intelligence lifecycle, which encompasses several key stages:
- Direction: Setting the strategic direction and objectives of the CTI function.
- Collection: Gathering data and intelligence from various sources, including automated and non-automated channels.
- Processing: Organising and structuring collected information for analysis.
- Analysis: Examining data to identify threats, vulnerabilities, and potential risks.
- Dissemination: Sharing intelligence and insights with relevant stakeholders for informed decision-making.
- Feedback: Incorporating feedback and lessons learned to continually improve the CTI process.
For more detailed information on establishing CTI lifecycle read here.